Your operational systems that run your day-to-day business are usually well-protected. System access is sophistically controlled, and firewalls enclose the heart of your IT environment. But when it comes to older IT systems, there might be vulnerabilities. What if some legacy systems reside outside your safety net, somewhat forgotten, even ignored? Maybe there were money-saving considerations in play not to include these systems within the high-protection cybersecurity environment. As such, intruders might be able to break in and steal valuable data easily: personal information of clients or employees, email addresses, home locations, and even credit card information.
Old legacy systems mostly represent just a cost block on the balance sheet. They are accessed only on infrequent occasions, with accessibility still ensured for business analysts. Often, employees, when switching roles, pass on data access authorizations to their successors. Or access IDs are simply forgotten, which opens up opportunities for data breaches and unauthorized access. Additionally, these old systems need updates from the software vendors regularly with patches and software releases to fix security loopholes. For example, more than 100 million Windows-7 PCs are still in use today. Keeping old systems updated on all software layers costs manpower, skills, and license fees for protective software. When considering 100s of legacy systems within large corporations, you get a glimpse of why I referred to the cost block on the balance sheet before.
While the first focus of cyber threat prevention lies in technology, the people layer represents an even greater risk level for security breaches. Calling it Social Engineering, the threats grow multifold. While larger corporations add cybersecurity training on the yearly curriculum for all employees, the phishing attacks still happen – and sometimes, they get trapped with a well-engineered cyber-attack. Of course, your operational business systems show the central core of the training; however, the old data, sometimes your crown jewels of the enterprise, might be neglected within the scope of learning, even not mentioned.
The cost of a data breach can explode in a matter of days. Think about a ransom attack. Somehow, the intruder got into your firewalls, through a technical loophole or via Social Engineering. Once inside, the trespasser takes hold of some of all of your systems, encrypts all data, and as such, makes your systems unusable for business operation. Locked down by a ransomware attack, you only have two options to respond: you pay the requested ransom, and you expect the cyber attacker provides you the decryption key to unlock the systems. I’d call it the principle of hope. Or you restore all systems and data to reinstate a previous situation, back to a point-in-time you know the attacker wasn’t in the system. Both options are very costly.
Sophos surveyed more than 5,400 IT decision-makers across 30 countries. Still, 37% of them reported hits by ransomware in 2021 (Figure 1).
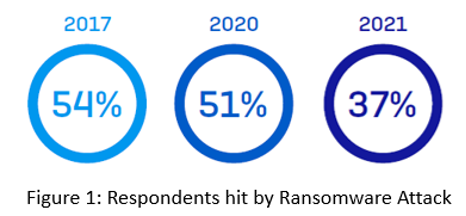
And once hit, the cost for remediation, including system downtime, people time, device cost, network cost, lost opportunities, and ransom paid grew to $1.85 M per case (Sophos, see Figure 2).

Larger corporations employ executives to focus only on cybersecurity. The CISO (Chief Security Information Officer) must detect and contain data breaches on operational systems and devices and old systems. IBM conducted a study with 537 organizations and concluded the time horizon from detecting a threat to containing it spans over 287 days (see IBM report on p.6). Also, they show, like the Sophos survey, a stunning average cost of a ransomware breach per case. These figures alone should be a wake-up call for everybody responsible for companies, lines of businesses, and IT operations: Get launched into action mode and review or revamp your cybersecurity safety net.
On the technical layer, permanent monitoring of all systems is required. The earlier you identify system behavior or network performance abnormalities, the better you can contain a possible cybersecurity attack. But monitoring also needs to include the people-layer. Software that scans emails and attachments for phishing and scamming strikes should represent your defense strategy’s minimum requirement.
Data breach violations also impose another layer of complexity. Within the US, the HIPAA (Health Insurance Portability and Accountability Act of 1996) regulations for the exchange of patient data impose penalties. What if your old systems contain doctors’ data or patients’ lab results? In the European Union, the GDPR (General Data Protection Regulation) penalizes companies when they ignore the data regulations with a fine of up to € 20m (Art.86 of the GDPR). Any company that runs data centers within the EU borders falls under these regulations, including Facebook, Google, Apple, and many other global cloud players. As the Deutsche Wohnen case shows, companies have to pay penalties even for breaching the privacy rights of EU citizens (The Transformers, p. 35).
Protecting the core data and Crown Jewels is undeniable urgent for enterprises of all sizes and private citizens. And once your business runs successfully over many years, don’t forget these Crown Jewels within the old legacy systems. The second-best way to prevent cyber-attacks is to go dark with these old systems, meaning to go offline from your network. But the best way to manage these old systems is to retire them and shut them off completely. It prevents data breaches, and it might save you significant money (JiVS use cases).

Author: Andreas Graesser, Chief Innovation Officer at innovad LLC. ( ag@innovad.io )
